Using airportd in Terminal on MacOS to get WiFi info
Today I was messaging with some other WiFi people about how they can get some visibility on what end users can see from their Macs without having to install software on their machines. This doesn't take away from using Adrian’s great AirTool or WiFi Explorer apps but it might be useful for end-users that either don’t have that software or if you need to work remotely via the command line (via SSH or something). If it’s your machine, just use those apps!
Anyway, Apple gives you the ability to tap into the Airport software on your Mac through Terminal using the airportd command. You can find it here:
/usr/libexec/airportdOne of the first things I do is make it so that I don’t have to type that whole thing out every time by running the following:
sudo ln -s /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport /usr/local/bin/airportthis now means you can just use:
airport in Terminal instead.
The two most common things I use are:
airport -sand
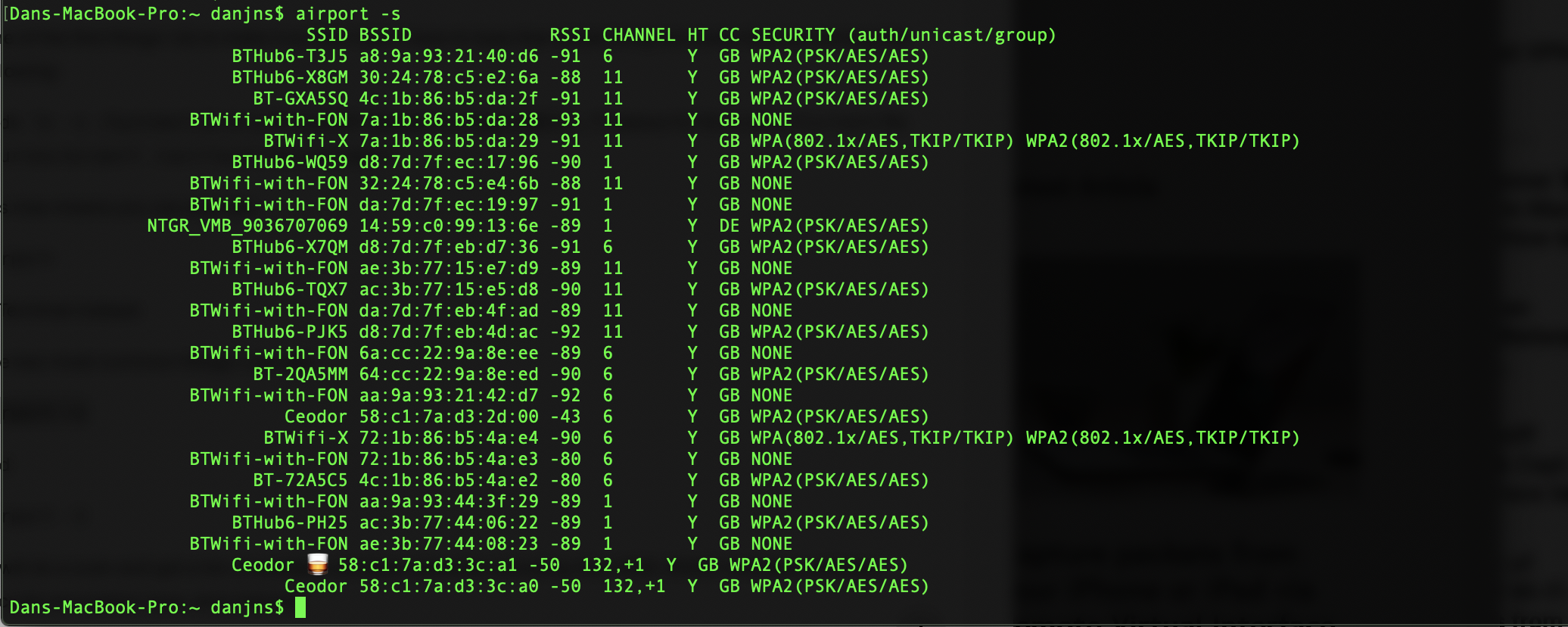
airport -I-s will do a scan and get a list of available wireless networks including their SSID, BSSID hardware address, security encryption type, and channel.
-I will which will give you information specific to the current wi-fi connection.
There is a whole bunch of extra stuff you can do but for now, I’ll show you how you can do a quick packet capture too. If you type:
airport sniffIt will start capturing traffic on your current channel. You can specify which channel to scan on too:
airport sniff 11airport sniff 132This will create a .cap file in your ‘/tmp’ directory (get to that by clicking on Finder and using “cmd + shift + G” and type “/tmp” in the window). In the Terminal session, you’ll see the file name that has been given to that capture. The easiest way to open that is to have Wireshark open and just drag the file into the Wireshark window.
If you want to explore what else you can do (and there is a lot!) just type:
airport -hAnd you’ll get the man page. Maybe one day I’ll work my way through them all…